Sandboxes
About Sandboxes
Sandboxes provide time-boxed, ephemeral AWS Management Console environments that expire automatically. A sandbox’s permissions are defined by a template and can range from full administrator access to least-privileged roles, depending on need. When a sandbox’s duration ends, access is revoked and all resources created inside the sandbox are cleaned up automatically—no user action required.
Important
Sandboxes are not enabled by default. They require a signed agreement because they incur additional costs for your organization. To enable Sandboxes for your organization, please reach out to Support.
Note
AWS region: Sandboxes currently run in us-east-1 only. Additional regions can be added if needed.
Key Concepts
Concept |
Description |
|---|---|
Sandbox |
A short-lived AWS environment defined by a |
Type |
The sandbox runtime. Two types are illustrated in the examples below:
|
Lifetime |
The initial duration of the sandbox (e.g., |
Lifetime Extension |
Optional, on-demand increments (e.g., |
Policy |
The permissions definition attached to the sandbox (for example, an IAM policy file like |
Provision Engine |
The engine used to orchestrate resources defined by the sandbox (e.g., |
Billing Limit |
A numeric cap used by the platform to help control costs attributed to the sandbox (e.g., |
Parameters |
Resource-specific inputs for the sandbox type (for example, EC2 instance settings: |
Region |
The AWS region in which sandboxes are created. Currently fixed to |
Prime |
Optional pre-warming configuration for sandboxes. When enabled, the platform creates “primed” sandboxes ahead of time to reduce wait time for learners. |
Lifecycle, Duration, and Cleanup
Start: Launch a sandbox from a
sandbox.ymltemplate. The environment and its access are created for the configuredlifetime.Extend: While running, you may extend the lifetime in
lifetime_extensionincrements, not exceedinglifetime_max.Expire & Clean: When the lifetime ends, access is revoked and resources created by the sandbox are cleaned up automatically—no user action required.
Creating a Sandbox and a Collection
Select Sandboxes from the Build menu, if that option is not available, Sandboxes are not enabled for your organization.
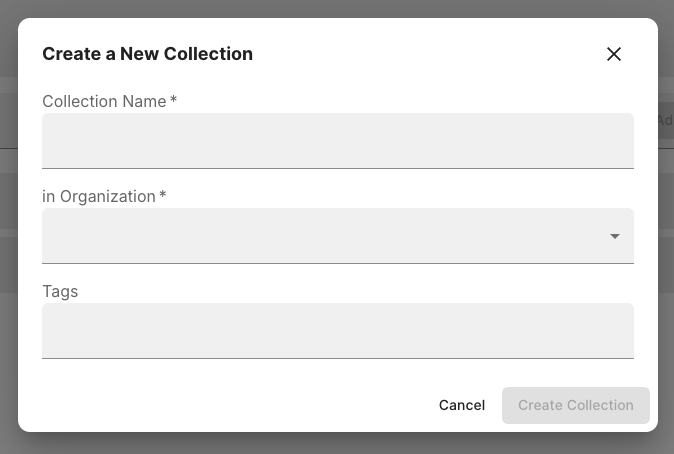
Then click the New Collection button in the top right. Give your collection a name and click Create Collection.
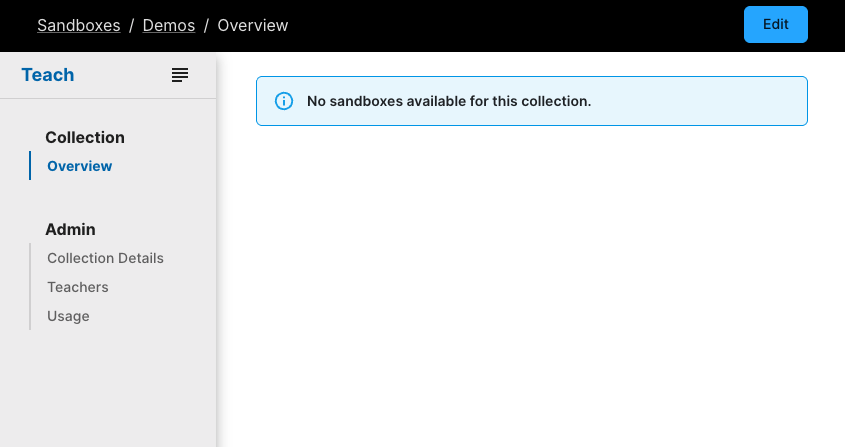
Once created, your new collection will open automatically. Click Edit to start creating sandboxes. The section below explains how to get started quickly.
Sandbox Configuration (sandbox.yml)
Define sandboxes in YAML, one sandbox per folder. The best starting point is using this command to get four working examples you can adapt:
git clone https://github.com/codio-content/sandboxes_examples.git .
Important
The command above will copy the repository to your current directory. Make sure your folder is empty.
Configuration Reference
Top-level keys
Key |
Type |
Required |
Description |
|---|---|---|---|
|
string |
Yes |
Schema version of the sandbox definition (e.g., |
|
enum |
Yes |
Sandbox runtime type. Supported in examples: |
|
mapping |
Yes |
Configuration block that defines lifetime behavior, permissions, provisioning engine, and resource parameters. |
|
mapping |
No |
Optional pre-warming configuration for any sandbox type. Supports priming continuously or on scheduled UTC start dates. |
settings (common)
Key |
Type |
Required |
Description |
|---|---|---|---|
|
string |
Yes |
Initial duration of the sandbox (e.g., |
|
string |
No |
Increment applied when extending a running sandbox (e.g., |
|
string |
No |
Maximum total runtime allowed for the sandbox (e.g., |
|
string |
Conditional |
Path or reference to the IAM policy that defines the sandbox’s permissions. Controls access level from full to least-privileged. |
|
string |
Conditional |
Infrastructure-as-Code engine used to orchestrate resources (e.g., |
|
number |
Optional |
Organizational cost control value associated with the sandbox. |
|
mapping |
Conditional |
Type-specific inputs. Required for |
settings.parameters for aws_ec2
After setting type to aws_ec2, configure the following parameters:
Key |
Type |
Required |
Description |
|---|---|---|---|
|
string |
Yes |
EC2 instance type to provision (e.g.,
|
|
string |
Yes |
AMI name or ID for the VM image. Examples:
|
|
integer (GB) |
Yes |
Root volume size in GiB for the instance (e.g., |
|
enum |
Optional |
Default access channel for the instance. Supported values in examples: |
prime (common)
Optionally prime (pre-warm) sandboxes to reduce learner wait time. Priming can be:
Continuous: Maintain a steady pool of primed sandboxes.
Date-based: Prime a specific number of sandboxes at specific UTC start times.
Note
For Continuous, sandboxes will start priming immediately after publishing the Collection. For Date-based this date specifies the time sandboxes will start priming, not when they will be ready.
Key |
Type |
Required |
Description |
|---|---|---|---|
|
enum |
Yes |
Priming mode. Supported values: |
|
integer |
Conditional |
Required when |
|
list |
Conditional |
Required when |
|
string (datetime, UTC) |
Conditional |
Required within each |
|
integer |
Conditional |
Required within each |
Permissions (Full to Least-Privileged)
Sandbox permissions are chosen by you via the attached policy:
To grant broad administrative capabilities, point
policyto an IAM policy that allows those actions.To enforce least-privileged access, supply a narrowly scoped policy granting only the minimum actions required.
This design lets you run anything from full AWS environments to tightly constrained labs, all with the same sandbox mechanism.
How can I create a policy?
Policies are an AWS concept. If you want to read more, please visit AWS’ guide to Policies and permissions and the IAM tutorial: Delegate access across AWS accounts using IAM roles.